Public announcement of the security issue. Actually, this is the easiest way. Windows, Ubuntu Linux and docker containers. A remote attacker could have sent carefully crafted requests causing a heap overflow, which may have led to the ability to execute arbitrary code on the server. A remote, authenticated, user could have triggered this flaw and executed arbitrary code on the server. Most of them were unauthenticated and version-based, written in python or bash. 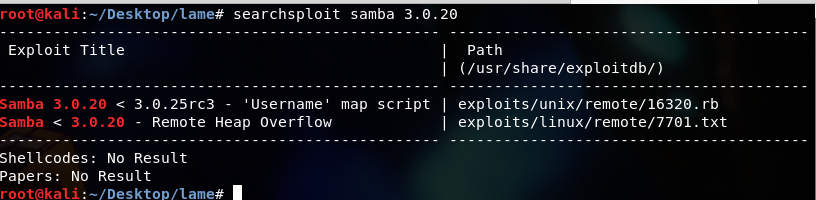
| Uploader: | Kiramar |
| Date Added: | 27 September 2011 |
| File Size: | 12.13 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 10545 |
| Price: | Free* [*Free Regsitration Required] |
Using GnuPG with Mozilla - http: Remote authenticated users could send specially 3.20 MS-RPC requests and execute arbitrary shell commands. Many students answered all the questions correctly, so it seems to me that the test wasn't bad.
If you sammba an owner of some content and want it to be removed, please mail to content vulners. I hope that all the students will successfully go through all the stages and with some of them we will meet at work or on internship.

So, those who are not really interested in the topic could choose something easy, and those who like this stuff could use this task to make an interesting research. No authentication is needed to exploit this vulnerability since this option is used to map usernames prior to authentication! Samba "username map script" Command Execution T Actually, this is the easiest way.
Internode :: Residential :: Entertainment :: File Download Mirror :: Directory Listing
Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. They either check the knowledge of some terms or definitions invented by some nonames or the knowledge of reference data, the markings of fire extinguishers in the CISSP exam, for example.
By sending a specially crafted RPC request, an attacker could overflow the buffer and execute arbitrary code. I hope the students asmba their fun too.
They registered Nessus Home on their own .30.20 used it at home environment, so the license agreement was not violated. Public announcement of the security issue. A remote attacker could send specially crafted MS-RPC requests that could overwrite heap memory and execute arbitrary code.

Therefore, I want to share my impressions and some statistics. LoginError nothing, it either worked or it didn't ; end handler end end. In addition, patches are available to address this vulnerability in Samba sambz 3. A remote, authenticated attacker can exploit this via the use of shell metacharacters during login negotiations when the 'username map script' option is enabled, or during the invocation of other printer and file management MS-RPC calls.
Using specially- crafted RPC requests, an unauthenticated attacker could leverage these issues to run arbitrary code on the affected device or make unauthorized changes to its system configuration. Rapid7 Insight is your home for SecOps, equipping you with the visibility, analytics, and automation you need to unite your teams and sama efficiency.
Basically it is for motivating them to visit lectures. Technical details for overvulnerabilities and 3, exploits are available for security professionals and researchers to review.
View Cookie Policy for full details. A remote, authenticated, user could have triggered this flaw and executed arbitrary code on the server.
Index of /pub/SAMBA/Samba/stable
Quick Sa,ba Notification This site uses cookies, including for analytics, personalization, and advertising purposes. Remote exploit for unix platform", "modified": This vulnerability could allow a malicious user to escalate user privileges.

RPORT ] end def exploit connect lol? For more information or to change your cookie settings, click here. Our vulnerability and exploit database is updated frequently and contains the 3.020 recent security research. Initial defect disclosure to the security samba. The vector was not really matter.
Products The Rapid7 Insight Cloud.

Comments
Post a Comment